You need to read HTTPS traffic from your application, but it is encrypted? I might have a solution for you.
It happens to me from time to time that I need to debug some application’s HTTP traffic, but tcpdump PCAP contains encrypted HTTPS traffic.
There are two ways on how to deal with this problem:
- (Pre)-Master-Secret (SSLKEYLOGFILE) log file
- Server private key
(Pre)-Master-Secret (SSLKEYLOGFILE) log file
SSLKEYLOGFILE is a file that contains TLS session keys of our running applications. It isn’t created by default, but we can often force applications to dump these keys. For example, browsers can do it. Google SSLKEYLOGFILE browser name for more details.
extract-tls-secrets is a great tool for Java that allows extracting the shared TLS secrets. This tool can attach to a running Java process, which is very convenient.
Just download the JAR from GitHub and run the following commands.
To list the available process IDs:
java -jar extract-tls-secrets.jar list
Attach to the running process:
java -jar extract-tls-secrets.jar <pid> /tmp/secrets.log
All Java application TLS shared secrets should be dumped to the /tmp/secrets.log file now.
You can start tcpdump/Wireshark to capture traffic now.
The next step is to open the PCAP file with Wireshark and configure (Pre)-Master-Secret log file.
It can be found at the following path: Preferences > Protocols > TLS (SSL for older versions) > (Pre)-Master-Secret log filename.
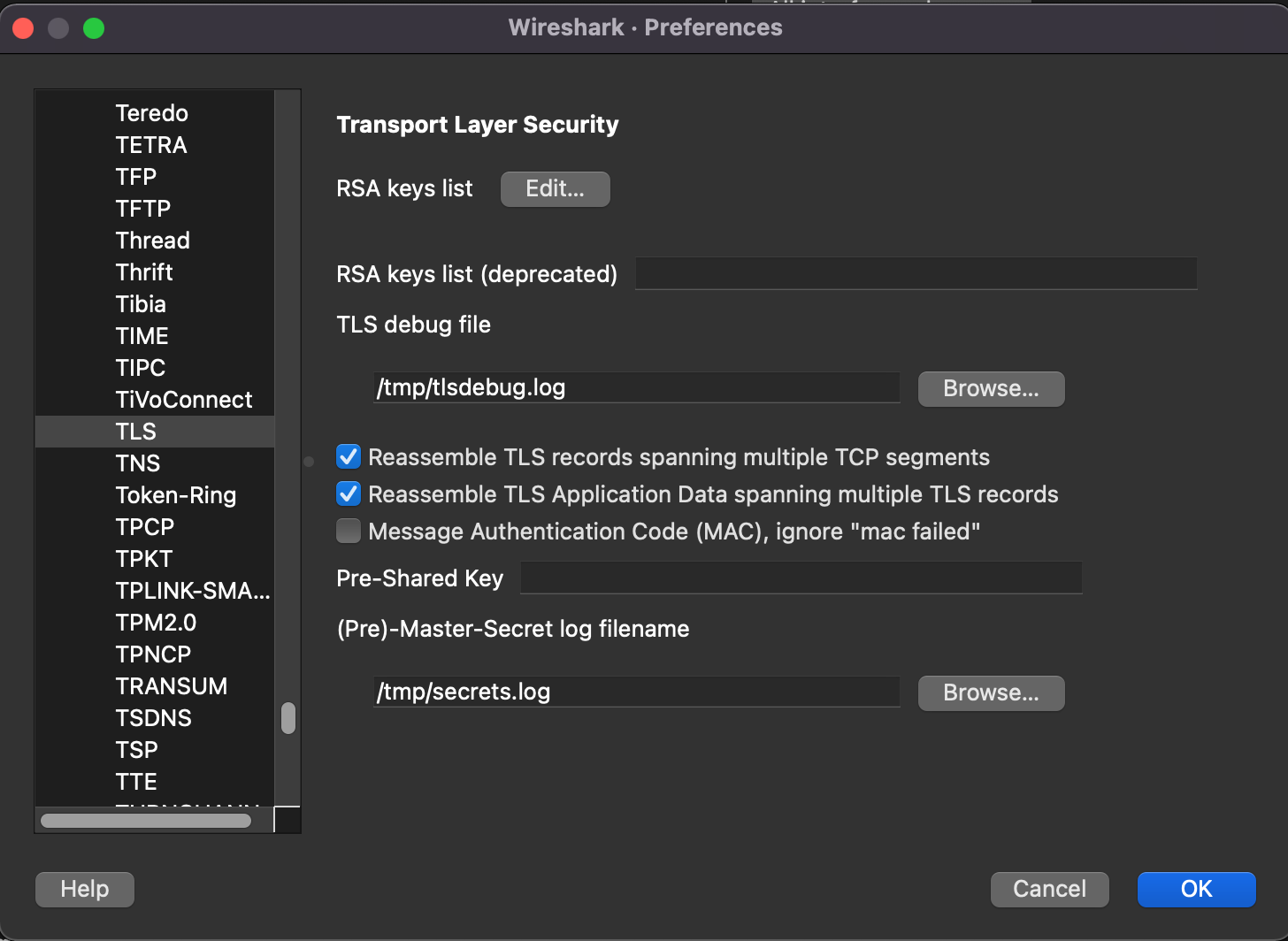
There might be a UI bug in Wireshark. If you don’t see decrypted traffic after selecting Follow/TLS Stream and none of the workarounds works (saving the capture file and reopening it or setting Reassemble TLS Application Data spanning multiple TLS records), then you can dump it to TLS debug file which can be configured in the same window as (Pre)-Master-Secret log file. This debug text file should contain decrypted traffic.
Server private key
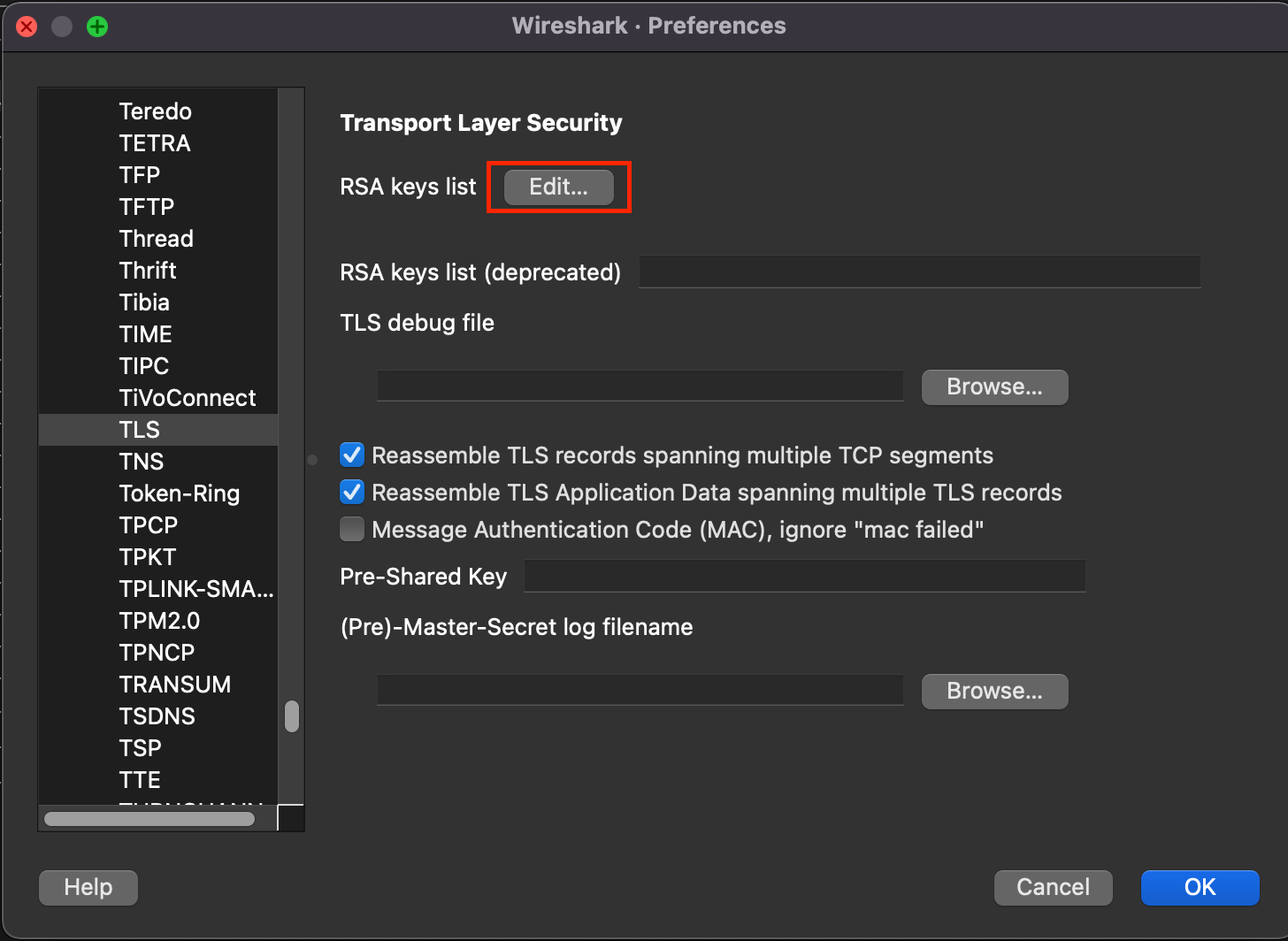
If you have a private key, you can use it to decrypt HTTPS traffic. All you have to do is to add this key to Wireshark.
Preferences > Protocols > TLS (SSL for older versions) > RSA key list edit
Fill the server address, port, protocol (probably http), key file path, and key password.
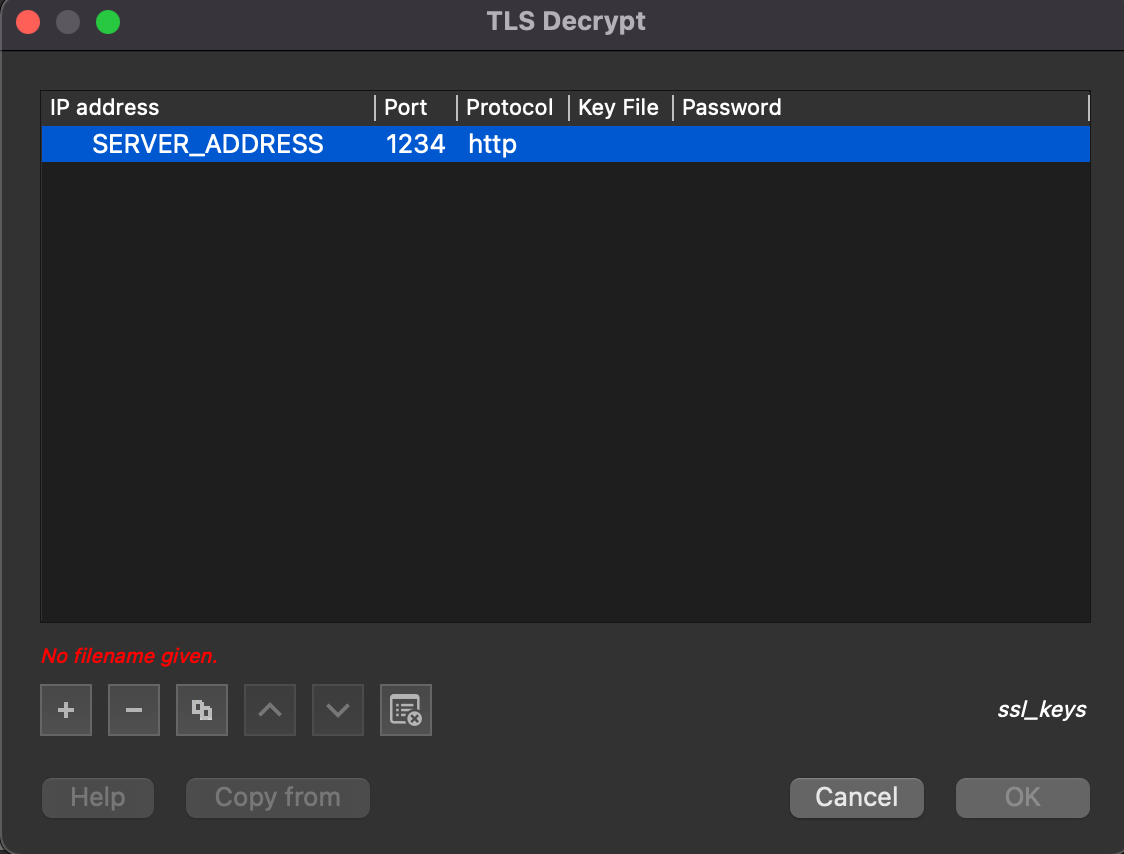
That’s it. The traffic should be decrypted. Just click Follow/TLS stream on the packet.
